# Configure SCIM in Okta
Workato supports the SCIM 2.0 protocol with the Okta identity provider.
# Prerequisites
- Your organization must have the Data Monitoring/Advanced Security & Compliance add-on.
- You must have SAML SSO successfully set up with your identity provider.
- You already configured SCIM in Workato.
# Configure SCIM
Log in to your Okta admin dashboard.
If you have already configured your Workato SAML app on Okta, locate the Workato SAML Application, and navigate there.
If you have not configured your Workato SAML app on Okta yet, create a new SAML 2.0 app before proceeding.
In the General tab, under App Settings, find the Provisioning field.
Select Enable SCIM Provisioning, and Save.
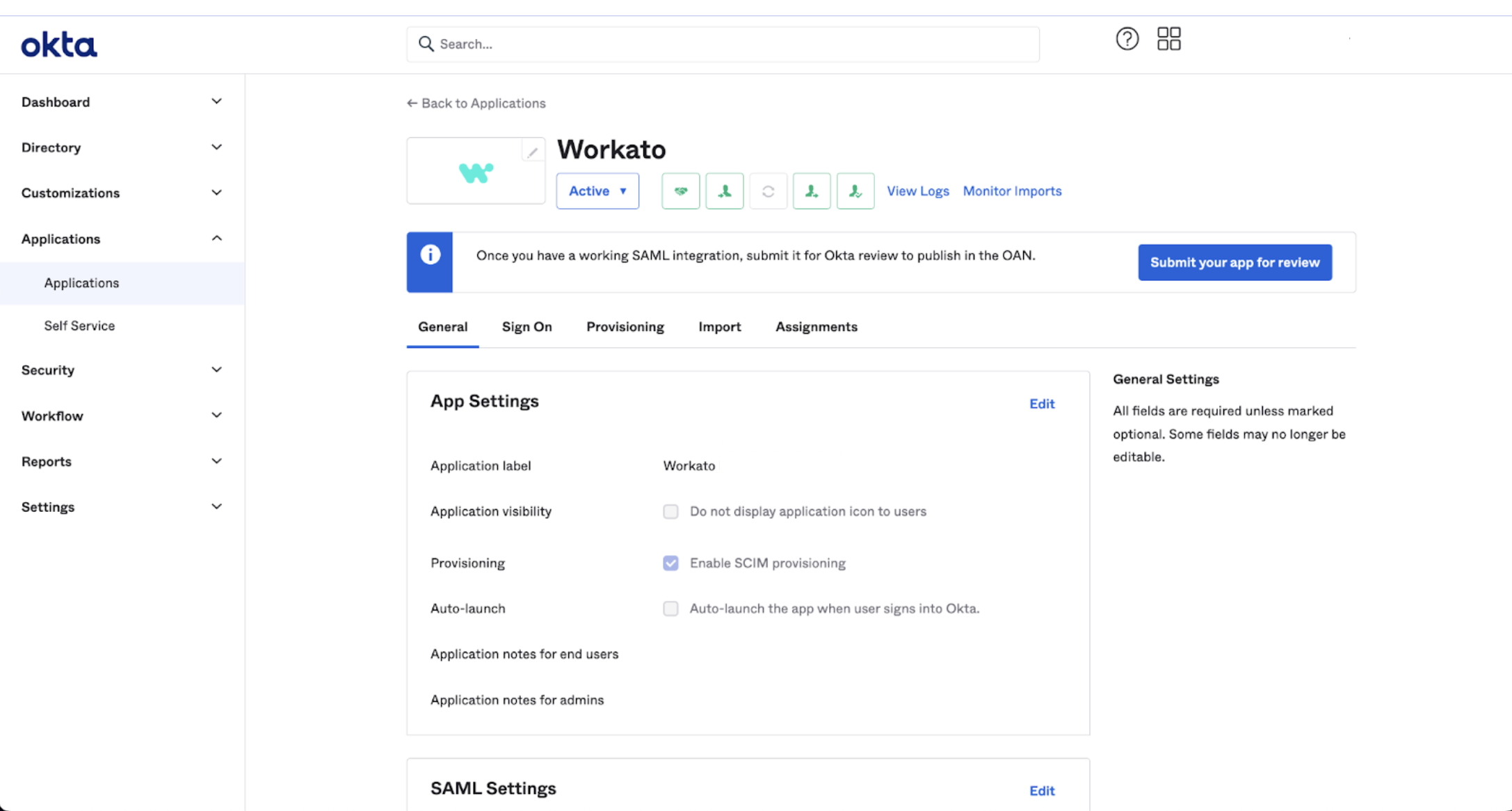 Enable SCIM provisioning
Enable SCIM provisioning
You can now see the new Provisioning tab on Okta.
In the SCIM Connection interface, specify the following:
- SCIM connector base URL
- This is the Base URL of the Workato SCIM API endpoint, that you copied when configuring SCIM in Workato.
- In this example, we use
https://workato.com/scim/v2. - Unique identifier field for users
- This is how we identify users both in Workato and in Okta.
- Here, we set the
userNamein Okta to contain the user’s email. - Supported provisioning actions
- Select the following actions:
- Import New Users and Profile Updates
- Push New Users
- Push Profile Updates
- Authentication Mode
- Select HTTP Header.
- Authorization
- Set the Bearer field by pasting the SCIM token you copied when configuring SCIM in Workato.
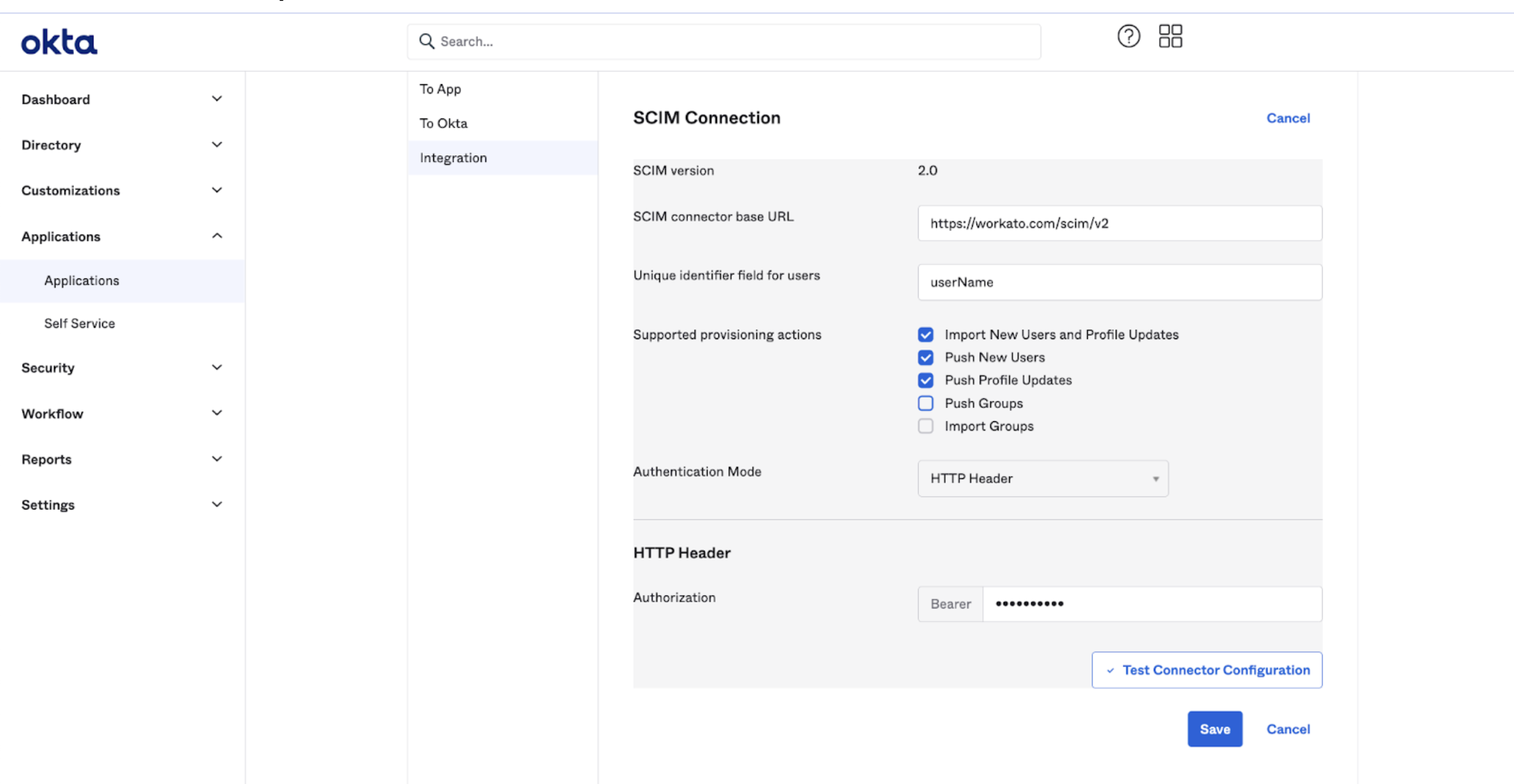 SCIM setup details
SCIM setup details
Click Test Connector Configuration to determine if your setup is correct.
When the test runs successfully, Okta displays the status of the connection and the supported SCIM provisioning actions.
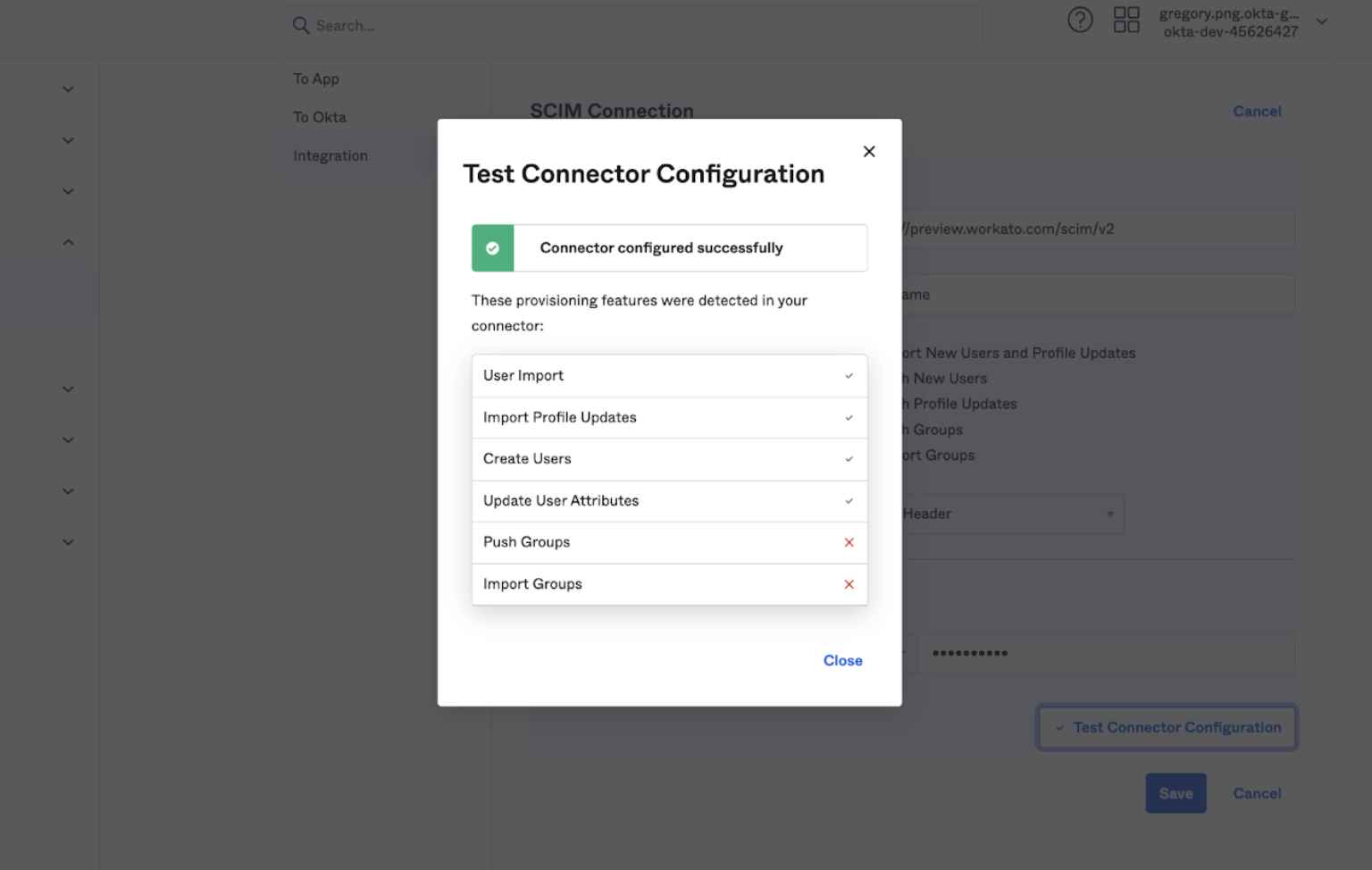 Successful SCIM setup in Okta
Successful SCIM setup in Okta
# Configure Workato role attributes for SCIM
After completing and verifying your SCIM configuration in Okta, you can see two additional options in the Application interface: To App and To Okta.
To sync Workato roles and other user attributes with Okta, you must select the following SCIM actions in the To App interface:
- Create Users
- Update User Attributes
- Deactivate Users
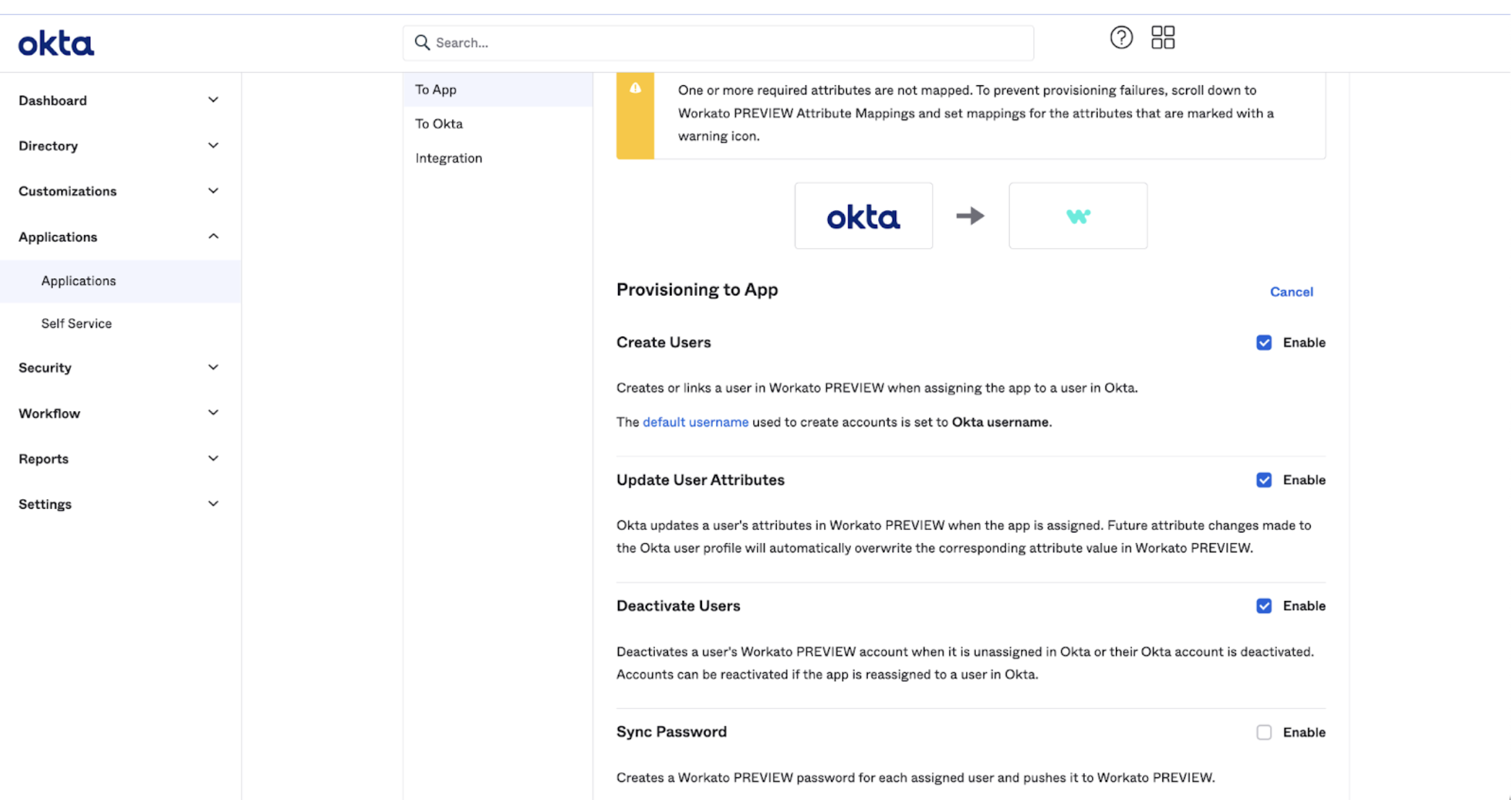 To App actions
To App actions
If you previously configured the workato_role, workato_role_test, and workato_role_prod custom attributes on the Workato App user profile, you must configure them again and include the additional external namespace.
This enables Okta to update these custom attributes as they change.
Navigate to the Profile Editor.
Select the Workato App User Profile.
Click Add attribute.
Add these values to the fields for
workato_role:
- Data type
String- Display Name
workato_role- Variable Name
workato_role- External Name
workato_role- External Namespace
urn:ietf:params:scim:schemas:workato:1.0:WorkatoRole- Attribute Members
- Define the enumerated list of values and add the attribute members; these are the roles that you can assign to users in Workato. For example,
Admin ,Analyst ,Operator , <No access , and custom roles. - Attribute
- Required. Ensure that this is checked.
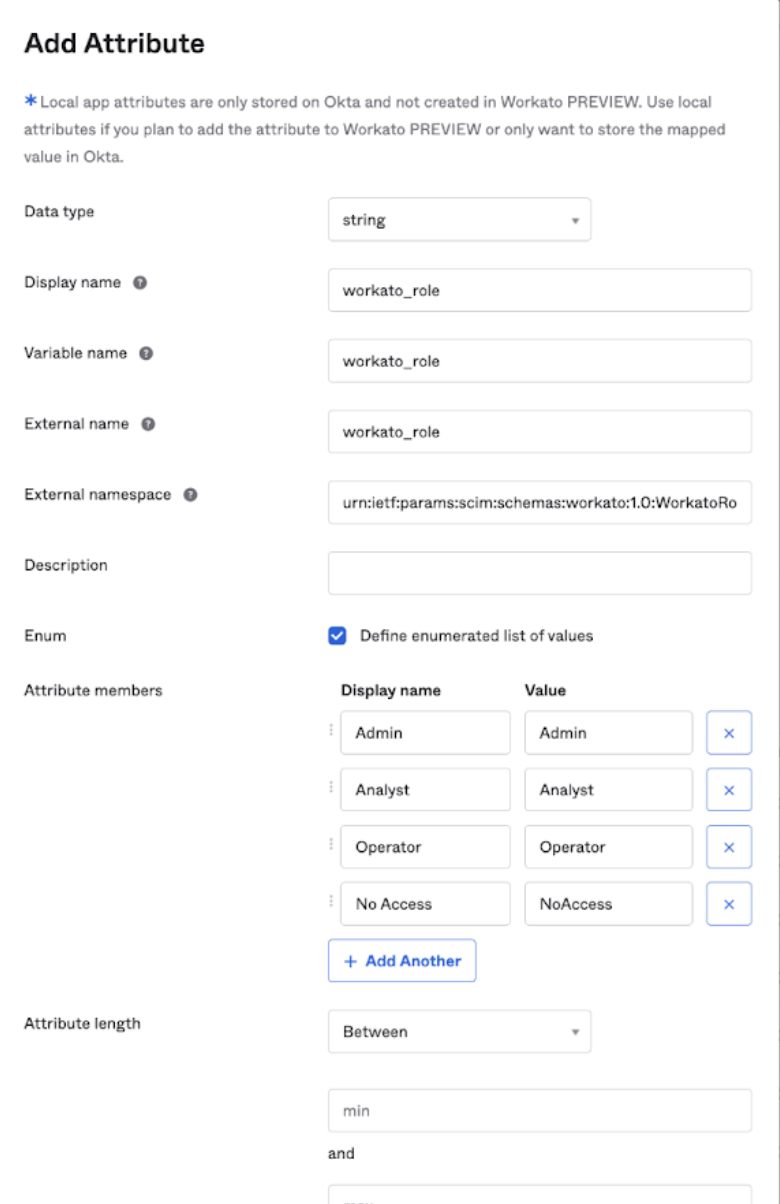 Configure workato_role
Configure workato_role
If your organization has the Environment feature in Workato, repeat this step for all environment-specific roles, such as workato_role_prod, workato_role_test, and for any additional custom roles.
Click Save.
Your configuration should resemble the following example:
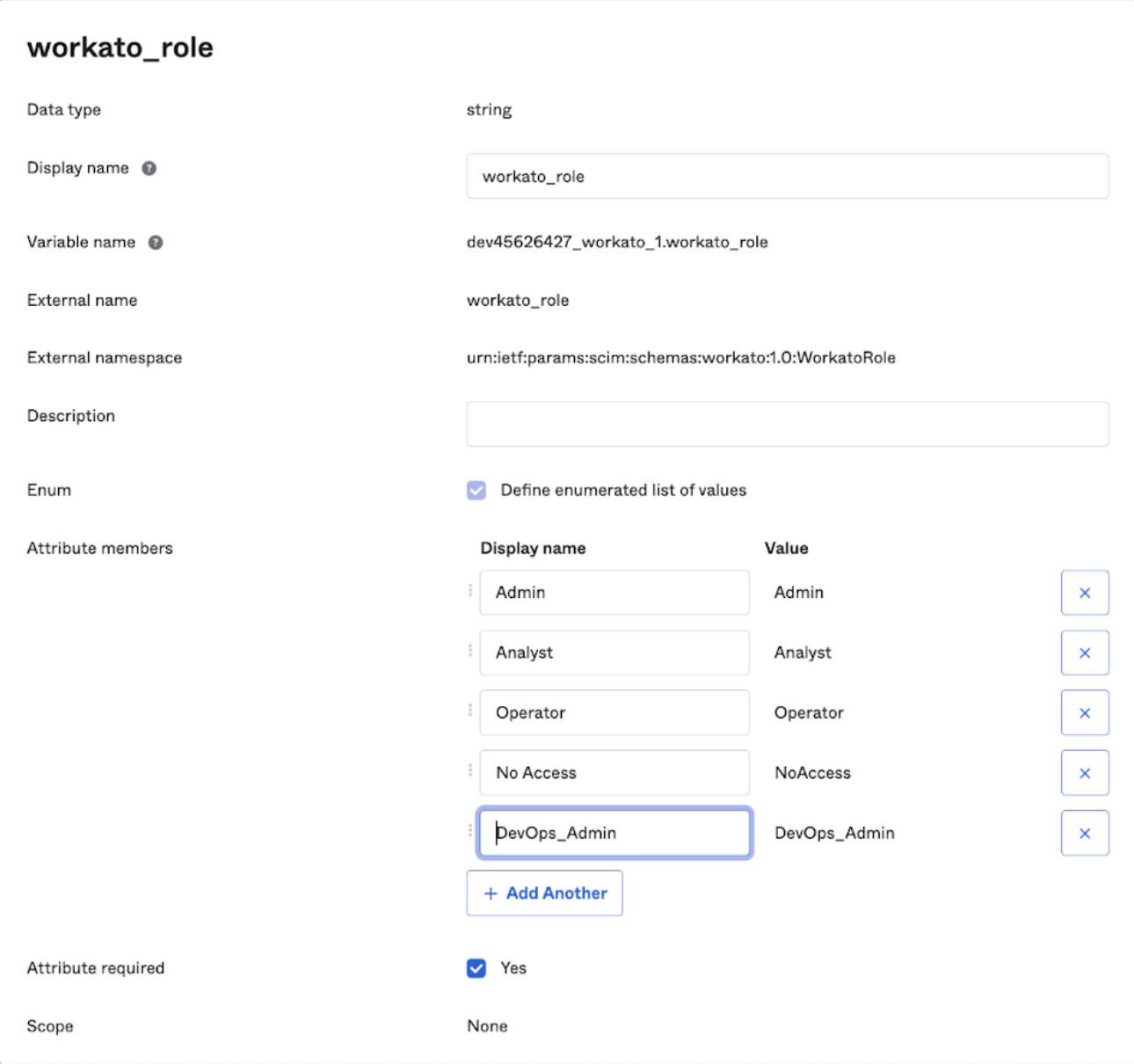 Complete configuration
Complete configuration
# Provision users
If you already have users assigned to your Workato application for SAML SSO, you can trigger a provisioning job to sync your existing users between Okta and Workato. This ensures that you don't unintentionally create duplicate accounts on your Workato workspace.
In the Assignments interface, Okta denotes the users that existed before you configured SCIM with a red exclamation mark icon.
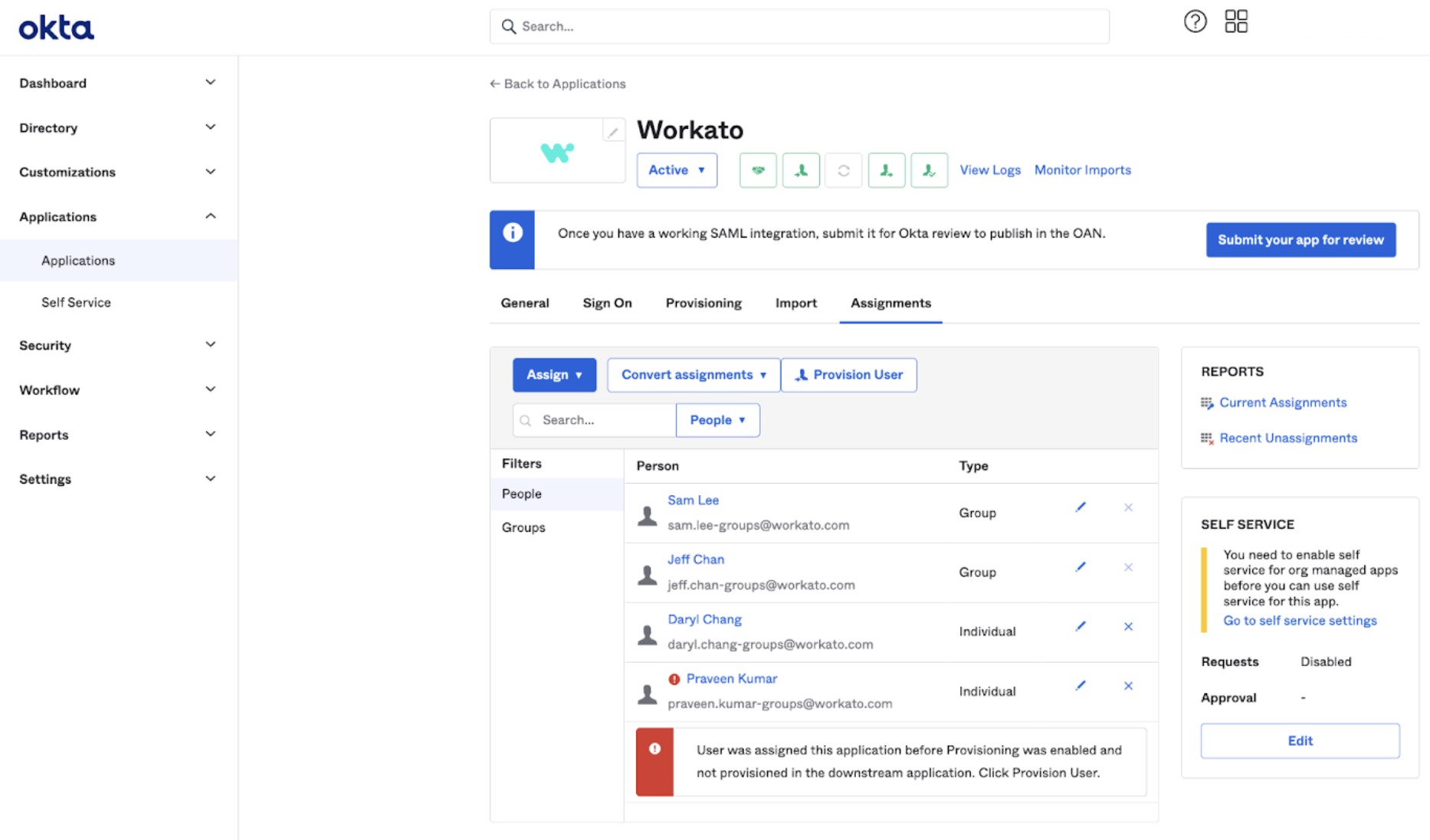 Existing users are not provisioned by SCIM
Existing users are not provisioned by SCIM
To trigger a provisioning cycle, click Provision User.
The system notifies you that it will sync the downstream app (Workato) and trigger user provisioning.
Click OK.
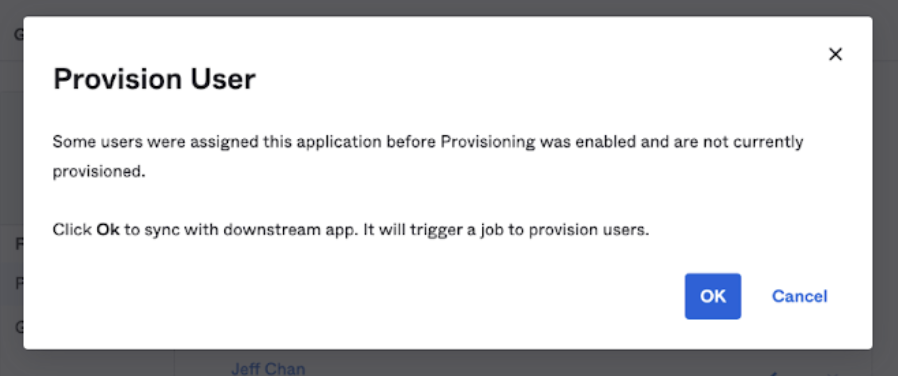 Confirm provisioning
Confirm provisioning
For new users, assign the application and specify the workato_role attribute values.
Alternatively, you may assign the application to a group, and then configure role values.
Navigate to Groups > Application > Assign Workato, and specify the attributes.
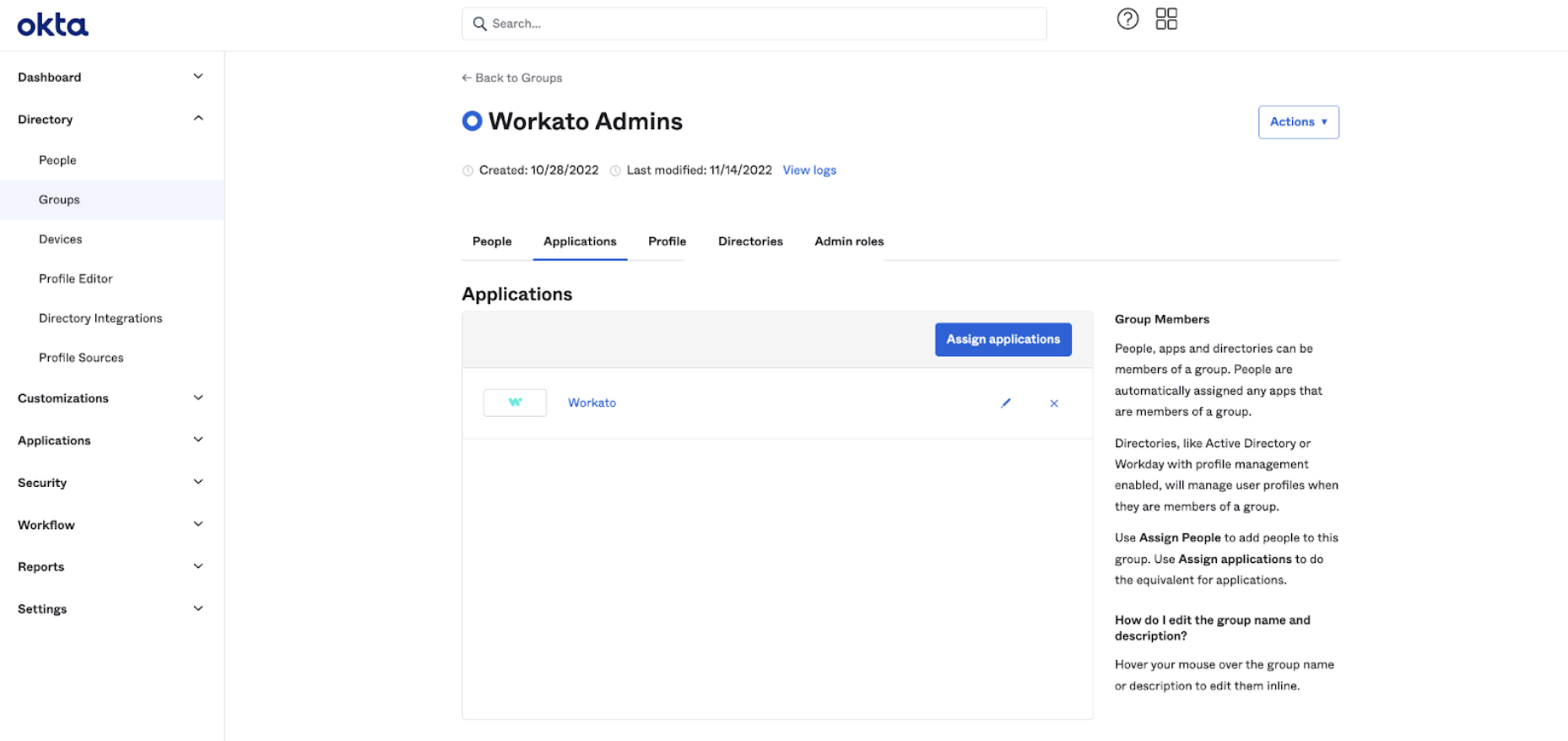 Configure groups
Configure groups
Workato sends an email invitation to the selected users. Instruct users to click the link in the email to verify their email address:
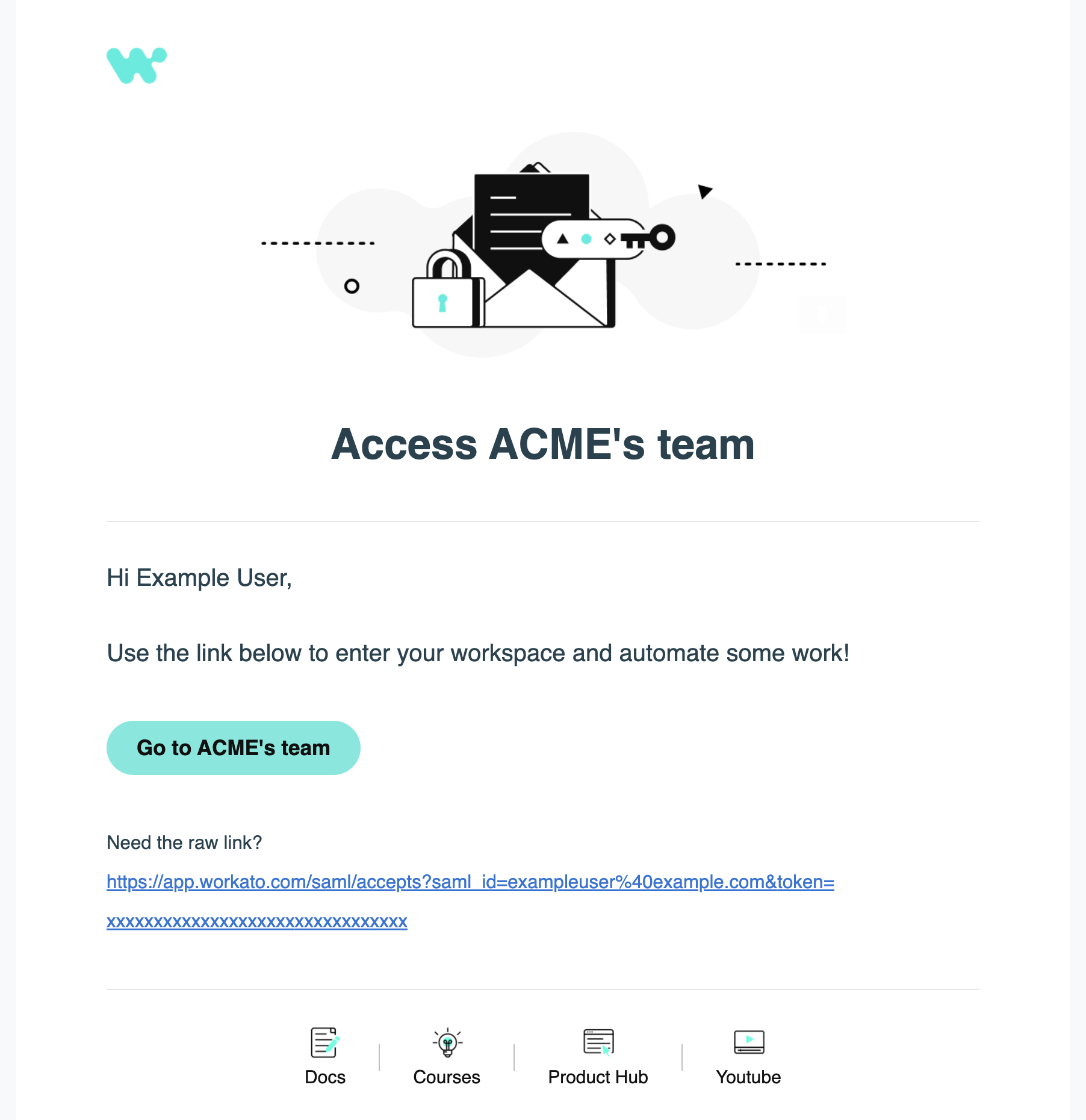 Email invitation to join a workspace
Email invitation to join a workspace
The collaborator can then sign in to the assigned workspace with the role(s) you configured.
TROUBLESHOOTING
If clicking on the invitation email redirects you to the Workato login page instead of your organization’s workspace, it is likely that you already have a Workato account associated with the same email. If you have forgotten your login credentials, reset your password.
You can check the Workato activity audit log to confirm the addition of the user:
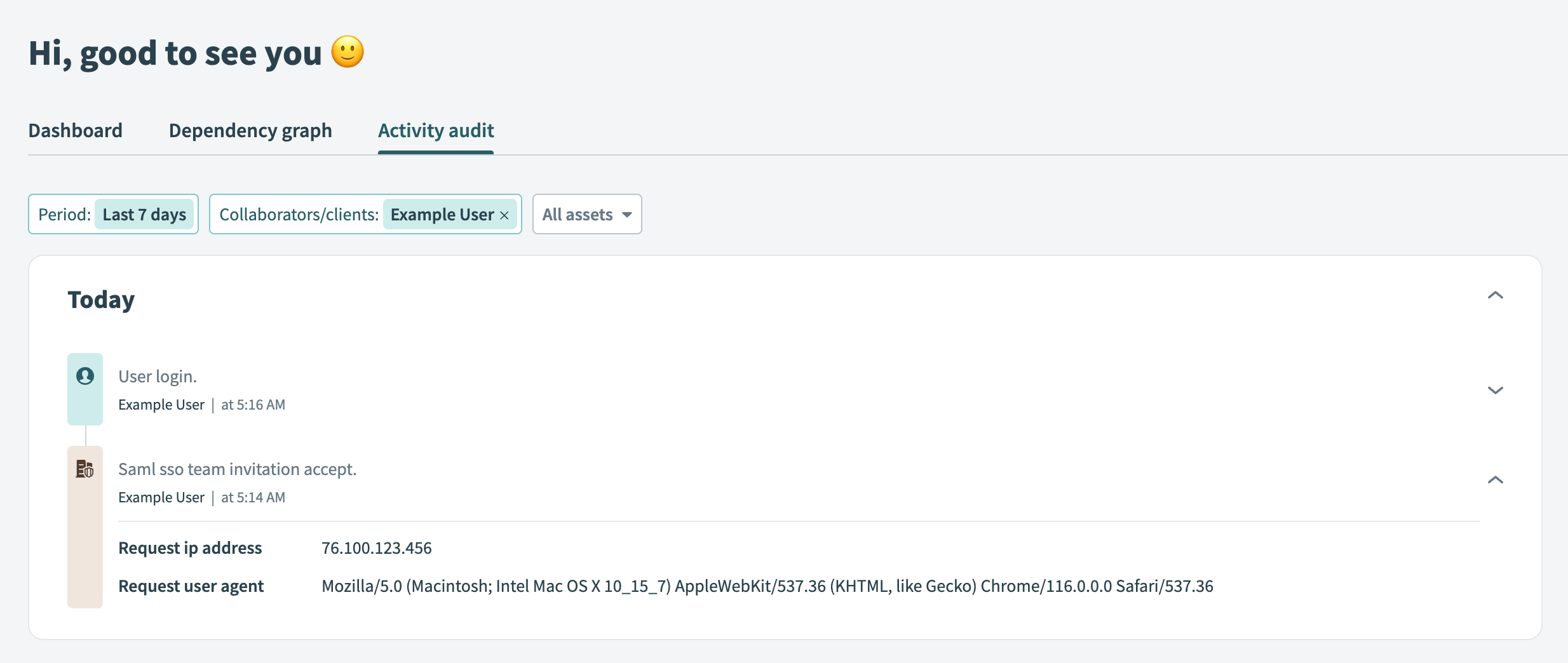 Activity audit log showing that a user has accepted an invitation
Activity audit log showing that a user has accepted an invitation
# Convert user assignments to group assignments
Consider a situation where you assigned a user to the Workato application individually, and now plan to manage them through groups on Okta. You must convert individual users to the group where they are assigned, so they get the roles that map from group attributes.
Navigate to the Workato application on Okta: Applications > Workato > Assignments.
Select Convert Assignments.
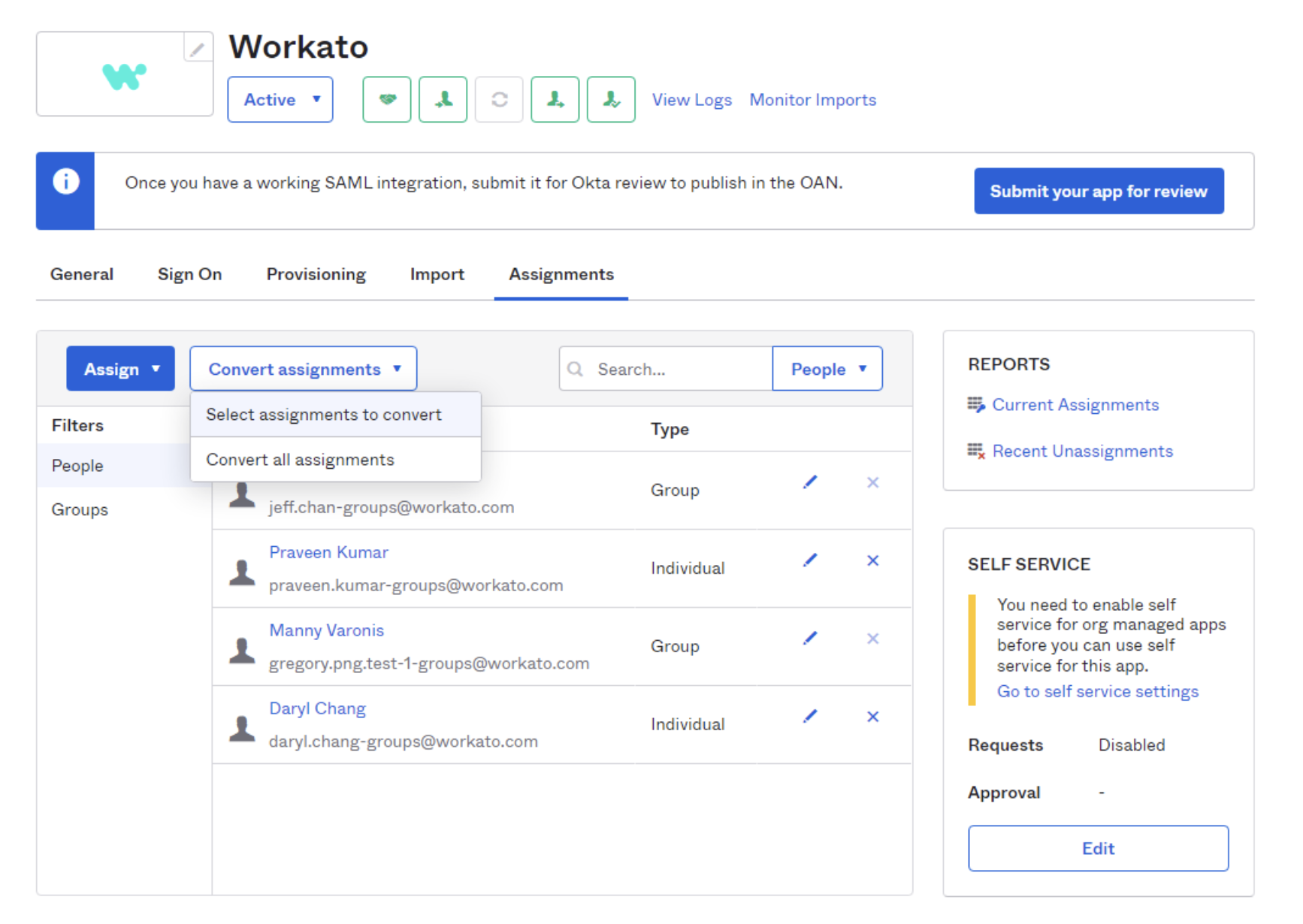 Convert assignments from user to group
Convert assignments from user to group
In the Select assignments to convert interface, select the individual user that you plan to convert from user to group management.
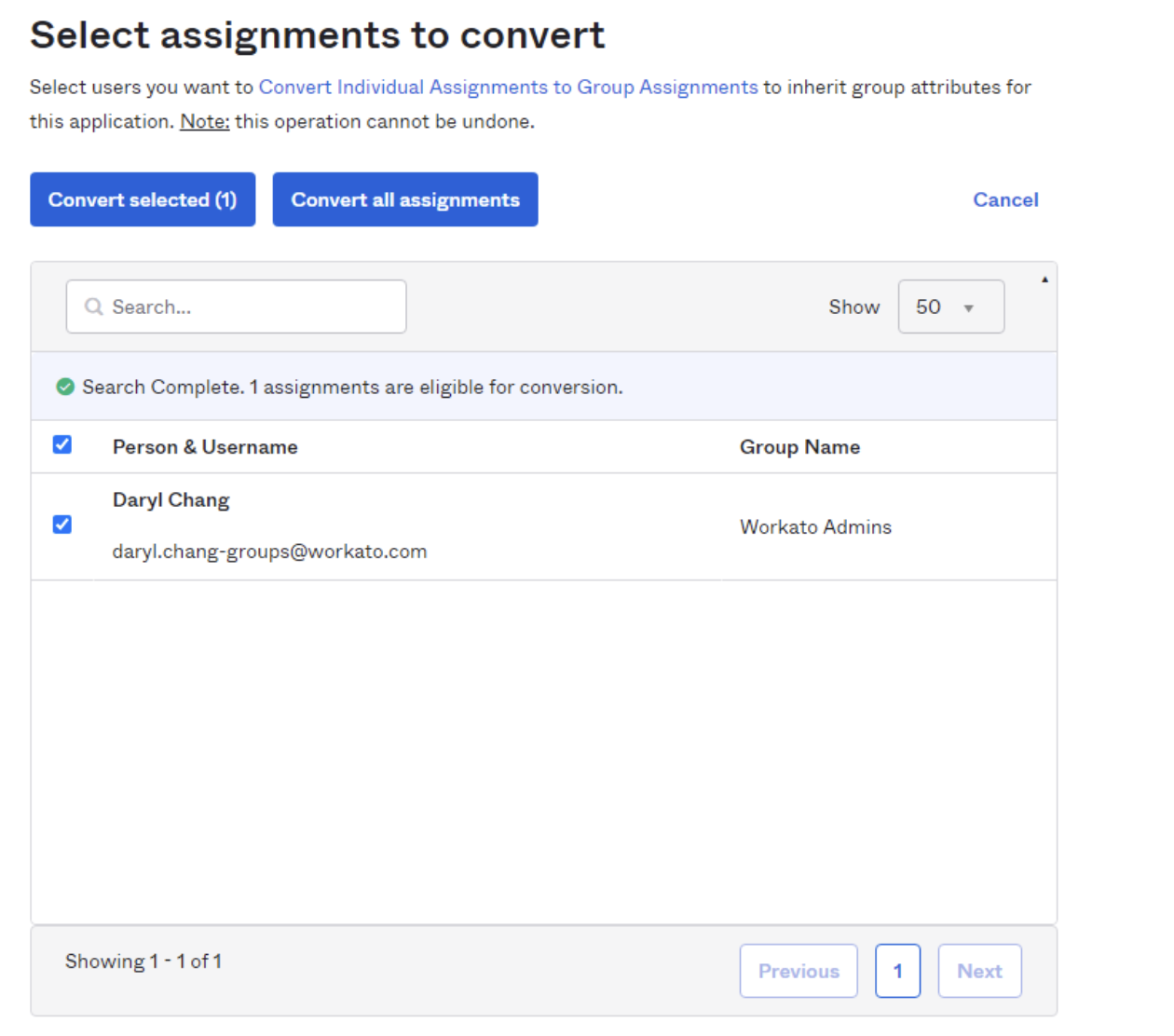 Select the user to convert to group management
Select the user to convert to group management
Click Convert selected.
When the conversion completes, Okta displays a successful conversion message.
# Update users
In contrast to SAML, role updates through SCIM occur immediately.
If a user has an active session, updating their role through SCIM triggers a role change immediately. So, the next action the user takes in Workato updates their access privileges according to the rules specified in Okta.
In Okta, navigate to Applications > Workato > Assignments > Select user.
Update the role values and click Save.
This action triggers a user update call to Workato through SCIM, and updates the user’s role.
To verify new members on Workato after provisioning them through SCIM, you can check the collaborators team list.
You can also examine the activity-audit logs dashboard.
We denote changes made through SCIM as scim_auto_sync.
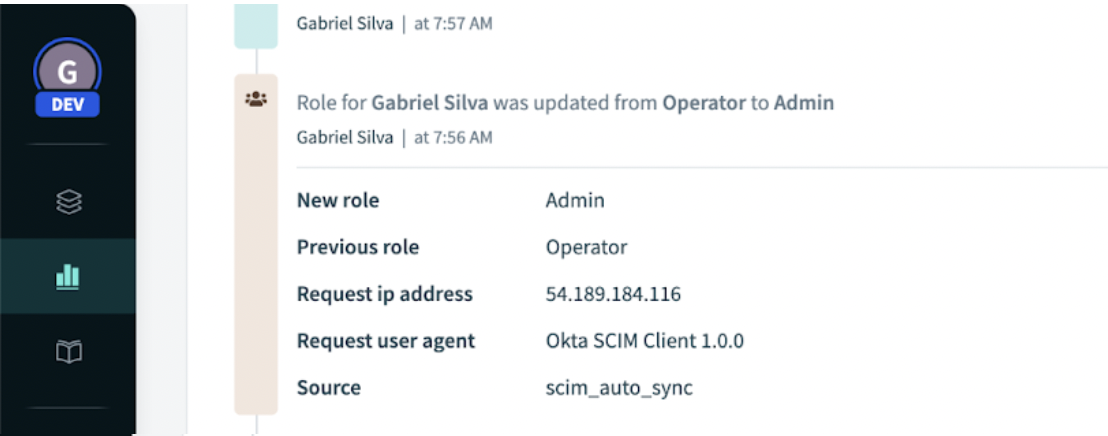 Confirming role change through SCIM
Confirming role change through SCIM
# Deprovision users
You can deprovision users directly in the Okta admin dashboard.
In Okta, a deprovisioning event can be any of the following actions:
- User suspension
- User deactivation
- App access removed
In Workato, a user is deprovisioned from your Workato workspace in any of the following scenarios:
- User is suspended in Okta
- User is deactivated in Okta
- Workato app is removed from the user
In all these situations, the user cannot access the Workato workspace. The user’s recipes and connections remain available to the rest of the team.
The user may be re-provisioned from Okta at a later time, and would retain their earlier privileges.
# Disabling SCIM
To disable SCIM, follow these steps in Okta. Alternatively, you can disable SCIM in Workato.:
In Okta, find the Workato application.
Navigate to General.
Disable SCIM by unselecting the Enable SCIM provisioning option, and then Confirm your action.
This action breaks your SCIM connection. User data cannot be synced between Okta and Workato.
Last updated: 2/20/2024, 5:01:26 PM