# Using Azure Key Vault secrets in connections
This guide demonstrates how to use secrets from your Azure Key Vault (opens new window) to configure Workato connections.
# Prerequisites
To complete the steps in this guide, you must have the following:
In Workato:
- An account with a successful workspace-level or project-level Azure Key Vault connection.
- A user role with Create and Edit Connections privileges.
In Microsoft Azure:
- Permissions allowing you to create Azure Key Vault secrets.
# Step 1: Add a secret to Azure Key Vault
Sign in to the Azure portal and navigate to Key vaults > {key vault name} > Secrets.
Select +Generate/Import.
On the Create a secret page, set Upload options to Manual.
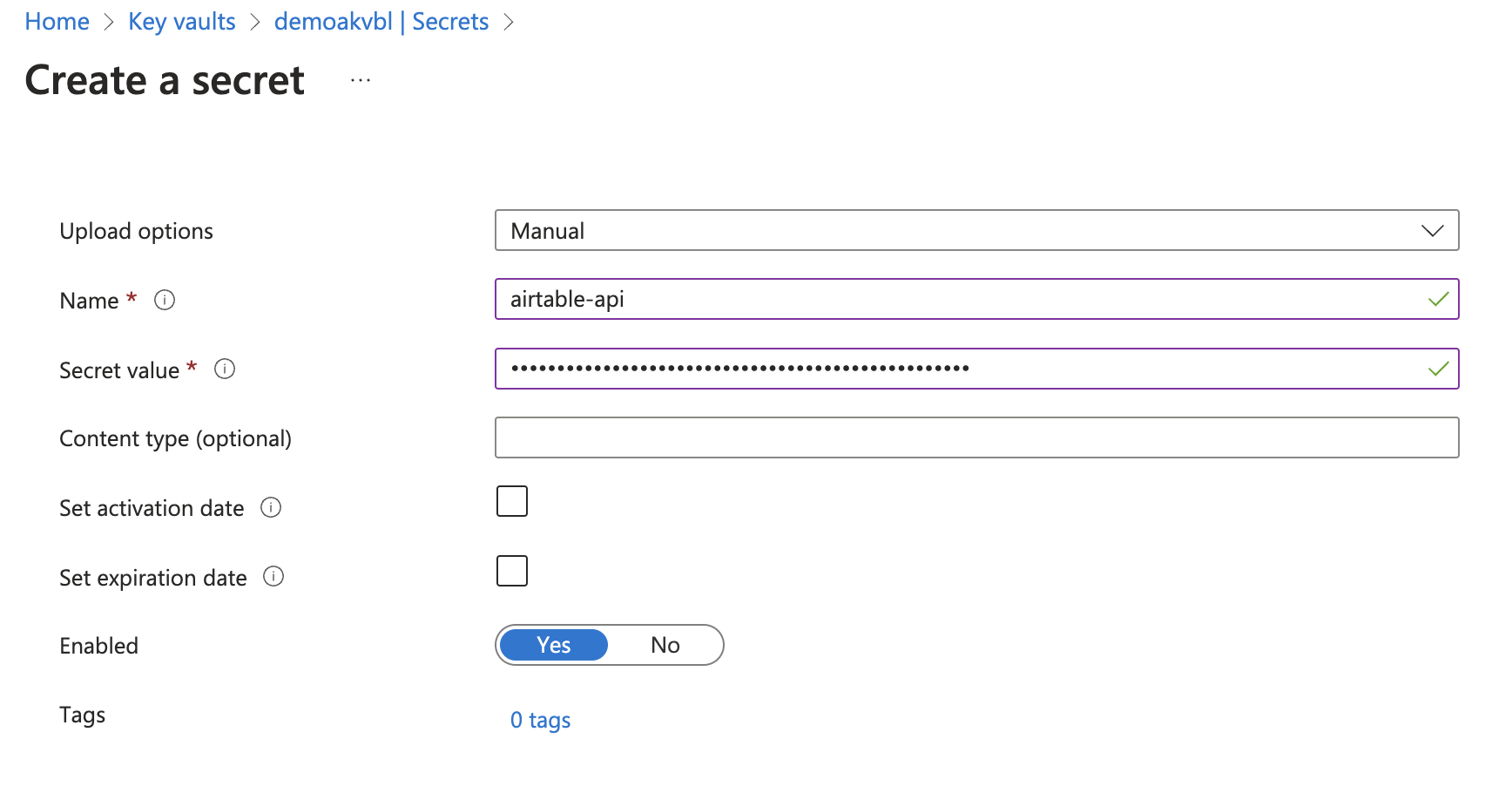 Create a secret in Azure Key Vault
Create a secret in Azure Key Vault
Enter a name for your secret that will help you remember what application it is for, such as airtable-api.
Enter the secret value. This is typically a password, API key, or other sensitive information.
Optionally, set the Content type, Activation date, and/or Expiration date.
Ensure the Enabled toggle is set to Yes.
Select Create.
# Step 2: Configure a Workato connection
In your Workato account, create a new connection or open the configuration page for an existing connection.
Azure Key Vault secrets in Workato connection credentials follow this syntax, where secret_name is the name of the secret you plan to use in Azure Key Vault:
{{workato:sm:<secret_name>}}
In the following example, the secret name is airtable-api:
{{workato:sm:airtable-api}}
In the connection's configuration page, paste this entire value into the appropriate field.
# Step 3: Complete your connection setup
Click Connect and verify that this connection is working.
# Troubleshooting
| Error message | How to fix it |
|---|---|
| The secret was not found in this key vault. | Ensure that your secret exists and you are connected to the right Azure Key Vault instance. |
The secret {{secret name}} has been disabled. Please ensure that it is enabled before re-trying. | Ensure that your secret is set to Enabled. |
| Caller is not authorized to perform action on resource. | Ensure that your Azure Active Directory app has the sufficient role or access policy and that your client secret is still valid. |
| Public network access to your Azure Key Vault is disabled. | Ensure that public access to your key vault (opens new window) is enabled. |
| Client address is not authorized and caller is not a trusted service. | Ensure that your network IP address has been added to your key vault's allowlist (opens new window). |
| Secret is expired. | Create a new secret version with a valid expiration date. |
| Secret is not activated. | Ensure that your secret's activation date is before the current date. |
| Failed to fetch secret from your vault. |
|
Last updated: 7/25/2023, 10:16:39 PM